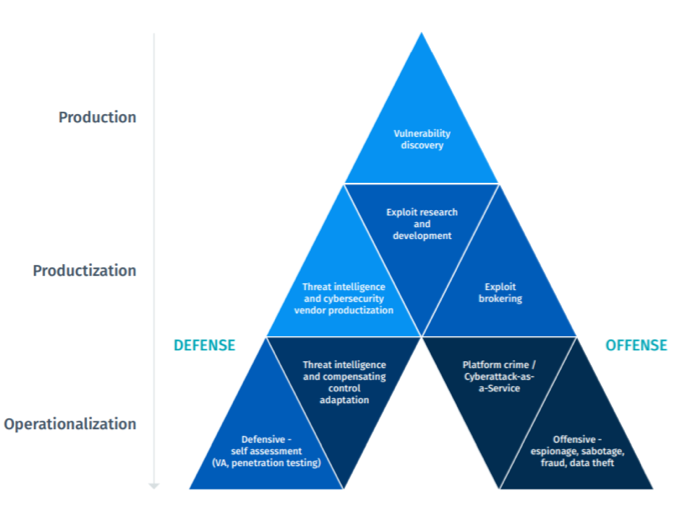
Supply chain vulnerability assessment: A network based visualization and clustering analysis approach - ScienceDirect

Amazon.com: Managing Supply Chain Risk and Vulnerability: Tools and Methods for Supply Chain Decision Makers: 9781848826335: Wu, Teresa, Blackhurst, Jennifer Vincent: Books

Minimizing the vulnerabilities of supply chain: A new framework for enhancing the resilience | Semantic Scholar


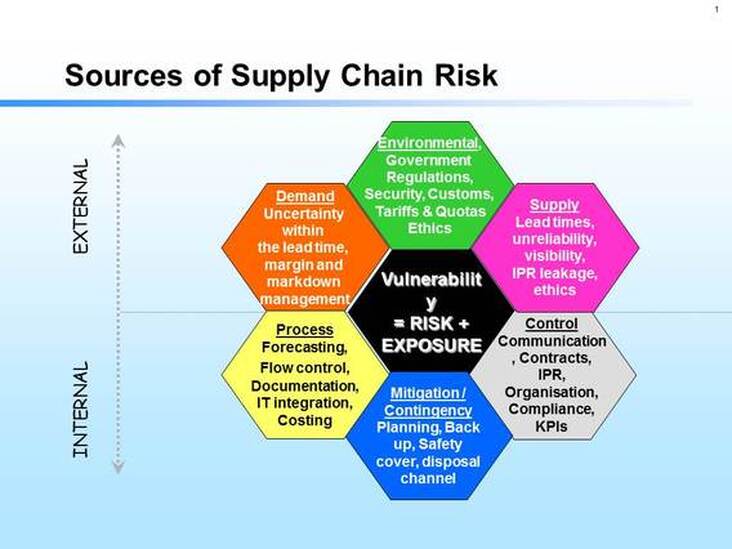
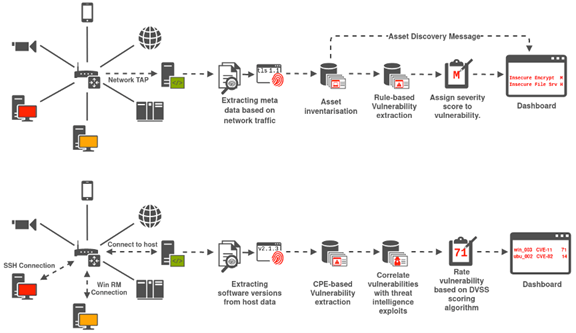
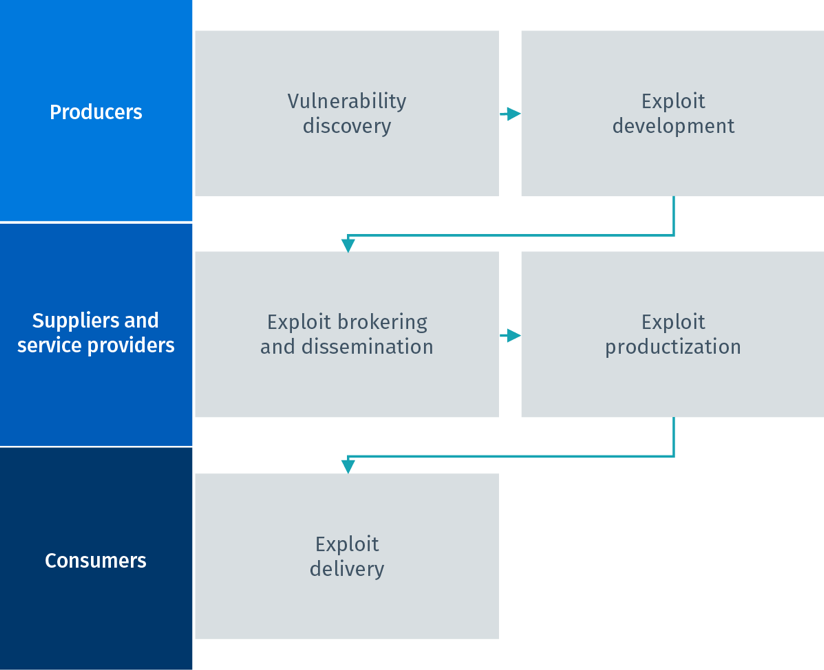







![PDF] An Integrated Method of Supply Chains Vulnerability Assessment | Semantic Scholar PDF] An Integrated Method of Supply Chains Vulnerability Assessment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/0601698c6153d456dabe6e73b83a7cf6979dab38/3-Figure1-1.png)